- To: submit@bugs.debian.org
- Subject: Kernel panic when rebooting a xen DomU
- From: Sylvain Beucler <sylvain.beucler@cliss21.org>
- Date: Tue, 23 Oct 2007 19:12:24 +0200
- Message-id: <471E2B78.6040302@cliss21.org>
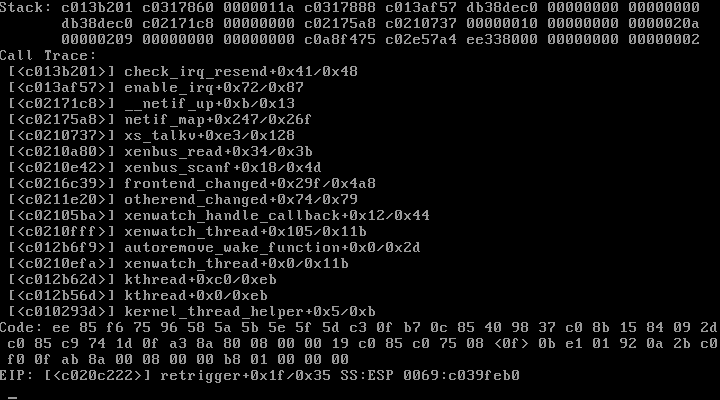
Package: linux-image-2.6.18-5-xen-686 Version: 2.6.18.dfsg.1-13etch4 On a Dell 2950 server, I rebooted a Xen instance: xm reboot backup then I remember checking the console for progress: xm console backup and when the DomU rebooted (or shortly after, I can't remember), I got a kernel panic (I got it through multiple "Message from syslogd@n8 at Tue Oct 23 15:48:26 2007 ..." over my SSH connection): n8 kernel: ------------[ cut here ]------------ n8 kernel: kernel BUG at drivers/xen/core/evtchn.c:481! n8 kernel: invalid opcode: 0000 [#1] n8 kernel: SMP n8 kernel: CPU: 5 n8 kernel: EIP is at retrigger+0x1f/0x35 n8 kernel: eax: 00000000 ebx: 02080000 ecx: 00000026 edx: f55f6000 n8 kernel: esi: c0317860 edi: 0000011a ebp: 00000000 esp: c039feb0 n8 kernel: ds: 007b es: 007b ss: 0069 n8 kernel: Process xenwatch (pid: 29, ti=c039e000 task=c0ead000 task.ti=c039e000) n8 kernel: Stack: c013b201 c0317860 0000011a c0317888 c013af57 db38dec0 00000000 00000000 n8 kernel: db38dec0 c02171c8 00000000 c02175a8 c0210737 00000010 00000000 0000020a n8 kernel: 00000209 00000000 00000000 c0a8f475 c02e57a4 ee338000 00000000 00000002 n8 kernel: Call Trace: n8 kernel: Code: ee 85 f6 75 96 58 5a 5b 5e 5f 5d c3 0f b7 0c 85 40 98 37 c0 8b 15 84 09 2d c0 85 c9 74 1d 0f a3 8a 80 08 00 00 19 c0 85 c0 75 08 <0f> 0b e1 01 92 0a 2b c0 f0 0f ab 8a 00 08 00 00 b8 01 00 00 00 n8 kernel: EIP: [<c020c222>] retrigger+0x1f/0x35 SS:ESP 0069:c039feb0 Attached is what I could get using the Remote Console Access (RAC). This is a screen capture of tty1. Also attached is the syslog around that time. The server froze and I had to reboot it. HTH, -- Sylvain
Oct 23 15:45:07 n8 snmpd[3047]: Connection from UDP: [212.99.96.245]:45629 Oct 23 15:45:08 n8 last message repeated 45 times Oct 23 15:48:24 n8 kernel: br-xen: port 2(vif1.0) entering disabled state Oct 23 15:48:24 n8 kernel: device vif1.0 left promiscuous mode Oct 23 15:48:24 n8 kernel: audit(1193147304.991:4): dev=vif1.0 prom=0 old_prom=256 auid=4294967295 Oct 23 15:48:24 n8 kernel: br-xen: port 2(vif1.0) entering disabled state Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: offline XENBUS_PATH=backend/vif/1/0 Oct 23 15:48:25 n8 logger: /etc/xen/scripts/block: remove XENBUS_PATH=backend/vbd/1/2049 Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: brctl delif br-xen vif1.0 failed Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: ifconfig vif1.0 down failed Oct 23 15:48:25 n8 logger: /etc/xen/scripts/xen-hotplug-cleanup: XENBUS_PATH=backend/vbd/1/2049 Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: Successful vif-bridge offline for vif1.0, bridge br-xen. Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: online XENBUS_PATH=backend/vif/2/0 Oct 23 15:48:25 n8 logger: /etc/xen/scripts/xen-hotplug-cleanup: XENBUS_PATH=backend/vif/1/0 Oct 23 15:48:25 n8 logger: /etc/xen/scripts/block: add XENBUS_PATH=backend/vbd/2/2049 Oct 23 15:48:25 n8 kernel: device vif2.0 entered promiscuous mode Oct 23 15:48:25 n8 kernel: audit(1193147305.747:5): dev=vif2.0 prom=256 old_prom=0 auid=4294967295 Oct 23 15:48:25 n8 kernel: ADDRCONF(NETDEV_UP): vif2.0: link is not ready Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: Successful vif-bridge online for vif2.0, bridge br-xen. Oct 23 15:48:25 n8 logger: /etc/xen/scripts/vif-bridge: Writing backend/vif/2/0/hotplug-status connected to xenstore. Oct 23 15:48:25 n8 logger: /etc/xen/scripts/block: Writing backend/vbd/2/2049/physical-device fe:0 to xenstore. Oct 23 15:48:25 n8 logger: /etc/xen/scripts/block: Writing backend/vbd/2/2049/hotplug-status connected to xenstore. Oct 23 15:48:26 n8 kernel: ------------[ cut here ]------------ Oct 23 15:48:26 n8 kernel: kernel BUG at drivers/xen/core/evtchn.c:481! Oct 23 15:48:26 n8 kernel: invalid opcode: 0000 [#1] Oct 23 15:48:26 n8 kernel: SMP Oct 23 15:48:26 n8 kernel: Modules linked in: xt_physdev iptable_filter ip_tables x_tables button ac battery ipv6 bridge sg sr_mod loop usb_storage 8250_pnp psmouse 8250 serial_core serio_raw rtc pcspkr shpchp pci_hotplug joydev evdev ext3 jbd mbcache usbhid dm_mirror dm_snapshot dm_mod ide_cd cdrom generic sd_mod piix ide_core ehci_hcd uhci_hcd usbcore bnx2 megaraid_sas scsi_mod thermal processor fan Oct 23 15:48:26 n8 kernel: CPU: 5 Oct 23 15:48:26 n8 kernel: EIP: 0061:[<c020c222>] Not tainted VLI Oct 23 15:48:26 n8 kernel: EFLAGS: 00010046 (2.6.18-5-xen-686 #1) Oct 23 15:48:26 n8 kernel: EIP is at retrigger+0x1f/0x35 Oct 23 15:48:26 n8 kernel: eax: 00000000 ebx: 02080000 ecx: 00000026 edx: f55f6000 Oct 23 15:48:26 n8 kernel: esi: c0317860 edi: 0000011a ebp: 00000000 esp: c039feb0 Oct 23 15:48:26 n8 kernel: ds: 007b es: 007b ss: 0069 Oct 23 15:48:26 n8 kernel: Process xenwatch (pid: 29, ti=c039e000 task=c0ead000 task.ti=c039e000) Oct 23 15:48:26 n8 kernel: Stack: c013b201 c0317860 0000011a c0317888 c013af57 db38dec0 00000000 00000000 Oct 23 15:48:26 n8 kernel: db38dec0 c02171c8 00000000 c02175a8 c0210737 00000010 00000000 0000020a Oct 23 15:48:26 n8 kernel: 00000209 00000000 00000000 c0a8f475 c02e57a4 ee338000 00000000 00000002 Oct 23 15:48:26 n8 kernel: Call Trace: Oct 23 15:48:26 n8 kernel: [<c013b201>] check_irq_resend+0x41/0x48 Oct 23 15:48:26 n8 kernel: [<c013af57>] enable_irq+0x72/0x87 Oct 23 15:48:26 n8 kernel: [<c02171c8>] __netif_up+0xb/0x13 Oct 23 15:48:26 n8 kernel: [<c02175a8>] netif_map+0x247/0x26f Oct 23 15:48:26 n8 kernel: [<c0210737>] xs_talkv+0xe3/0x128 Oct 23 15:48:26 n8 kernel: [<c0210a80>] xenbus_read+0x34/0x3b Oct 23 15:48:26 n8 kernel: [<c0210e42>] xenbus_scanf+0x18/0x4d Oct 23 15:48:26 n8 kernel: [<c0216c39>] frontend_changed+0x29f/0x4a8 Oct 23 15:48:26 n8 kernel: [<c0211e20>] otherend_changed+0x74/0x79 Oct 23 15:48:26 n8 kernel: [<c02105ba>] xenwatch_handle_callback+0x12/0x44 Oct 23 15:48:26 n8 kernel: [<c0210fff>] xenwatch_thread+0x105/0x11b Oct 23 15:48:26 n8 kernel: [<c012b6f9>] autoremove_wake_function+0x0/0x2d Oct 23 15:48:26 n8 kernel: [<c0210efa>] xenwatch_thread+0x0/0x11b Oct 23 15:48:26 n8 kernel: [<c012b62d>] kthread+0xc0/0xeb Oct 23 15:48:26 n8 kernel: [<c012b56d>] kthread+0x0/0xeb Oct 23 15:48:26 n8 kernel: [<c010293d>] kernel_thread_helper+0x5/0xb Oct 23 15:48:26 n8 kernel: Code: ee 85 f6 75 96 58 5a 5b 5e 5f 5d c3 0f b7 0c 85 40 98 37 c0 8b 15 84 09 2d c0 85 c9 74 1d 0f a3 8a 80 08 00 00 19 c0 85 c0 75 08 <0f> 0b e1 01 92 0a 2b c0 f0 0f ab 8a 00 08 00 00 b8 01 00 00 00 Oct 23 15:48:26 n8 kernel: EIP: [<c020c222>] retrigger+0x1f/0x35 SS:ESP 0069:c039feb0 Oct 23 15:57:06 n8 syslogd 1.4.1#18: restart.
--- End Message ---